Our Approach
MITRE’s Behavioral Sciences Approach to Building Insider Threat Indicators
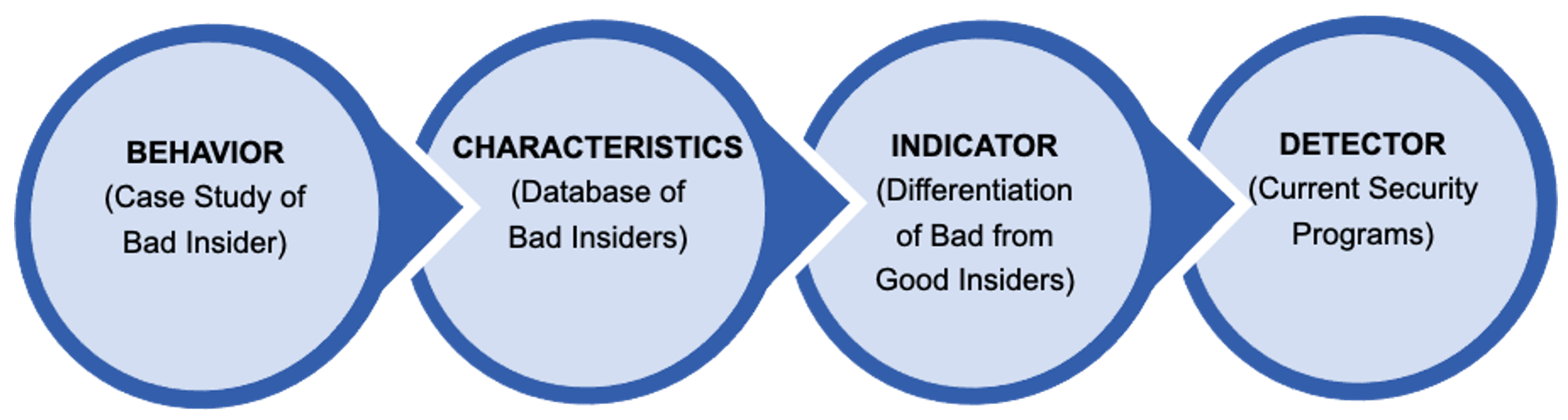
MITRE’s behavioral scientists are leading the insider threat community by generating potential risk indicators (PRIs) through the systematic, empirical study of behavior. Our approach distinguishes between case study behaviors, characteristics, indicators, and detectors. The distinction between those categories might appear obvious at first glance but there is a significant amount of confusion in the community. Currently, most insider threat practitioners think they are working with indicators when in fact they are working with case study behaviors and occasionally characteristics, which are not effective indicators.
Case studies behaviors are individual behaviors derived from a singular case study. Case studies are intriguing and useful for socializing and motivating action on insider threat but are not useful for proactively finding insiders. Many seemingly logical ‘indicators’ fail because they are based on singular case studies that do not distinguish whether a behavior or event in that case study was relevant to an individual’s malicious or non-malicious goals, nor whether that behavior or event was already frequent amongst the wider population. Instead, deriving behaviors from singular case studies simply results in organizations chasing the last insider but not finding the next.
Characteristics are patterns of similar behaviors across known bad insiders, which are identified by collating and analyzing data across a collection of many case studies. The main challenge in relying solely on characteristics for insider threat detection is that there is no baseline from which to compare to the general population. For example, characteristics such as high alcohol usage or high narcissism could emerge from analyzing patterns across dozens of case studies. However, both characteristics are so common within the wider, general population that neither are useful for identifying insider risk. Similarly, malicious employees exfiltrating data off network to send to competitors use many of the same behaviors as employees sending information off network to clients or customers. The similarity in these characteristics means that Insider Threat/Risk Programs become overwhelmed by a high number of false positives.
Indicators are the characteristics from known bad insiders that are distinct from the behaviors of the wider population within the organization. These indicators are researched and developed by comparing data-driven characteristics to the behaviors in the wider population to identify which behaviors are statistically different and meaningfully diagnostic for detecting risk. Generating robust indicators requires a large collection of case studies from which to derive characteristics, and a baseline of those behaviors from the general population to compare those characteristics to in order to identify risk indicators.
Detectors describe how to unobtrusively observe the data-driven indicators in cyber, physical, human, and organizational sensors available to Insider Threat/Risk Programs. These detectors should be developed based on real sensors and program data, which can be particularly challenging because many indicators are difficult to directly observe without engaging employee. Therefore, we have robust indicators identifying through research that do not have practical detectors yet.
